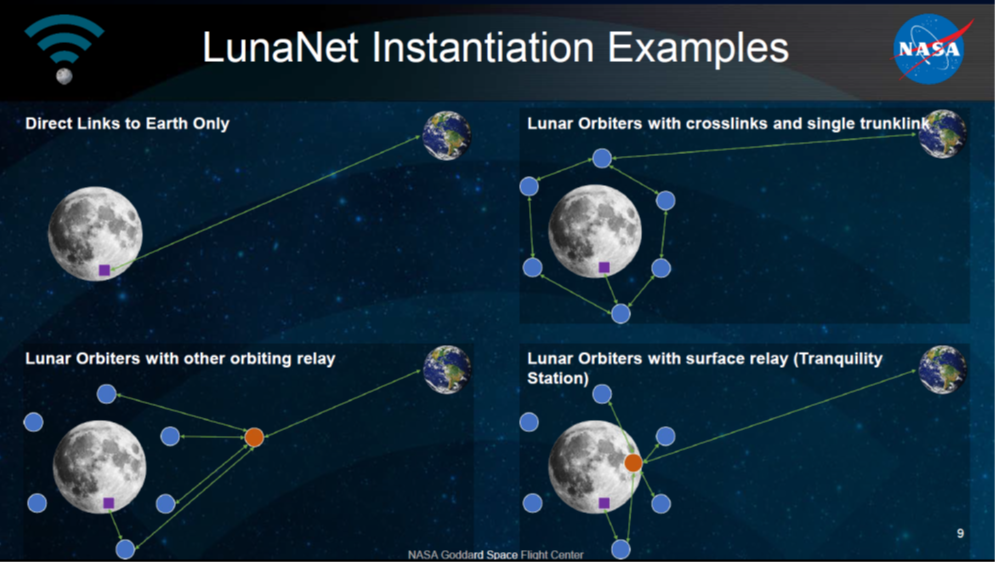
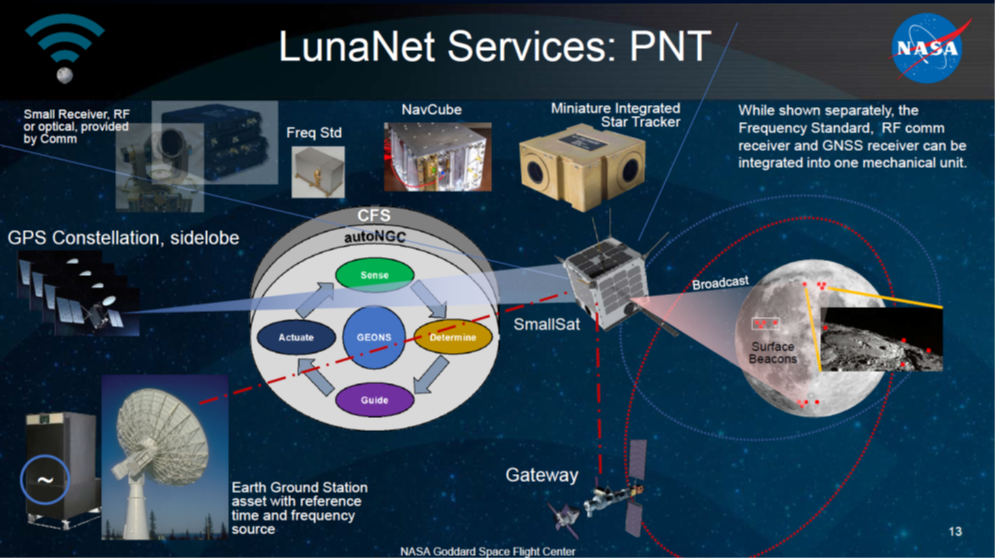
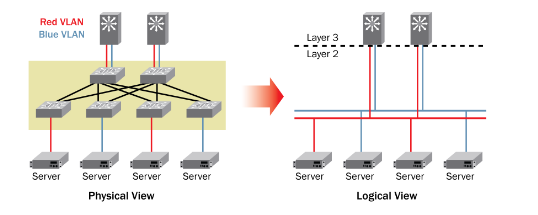
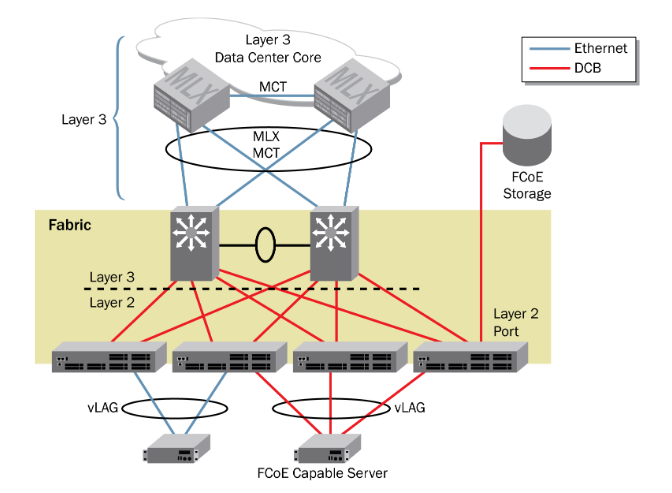
About Veeam Software
Veeam Software, Elite partner in the VMware Technology Alliance program, Microsoft partner and participant in the VMware Ready Management program, provides innovative software for VMware vSphere and VMware Infrastructure environments. For more information about Veeam Software, please visit www.veeam.com/pl.
Veeam Backup & Replication v7, v8 (New)
Number 1 for backing up virtual machines
Veeam® Backup & Replication ™ makes it possible efficient, easy-to-use and affordable recovery virtualized applications and data. This comprehensive solution combines the functions of data backup and replication, increases the usefulness of backups and offers an innovative method of data protection in VMware vSphere and Microsoft Hyper-V environments. With a single license, you can use the integrated console to operate the entire virtual infrastructure, using industry-leading features such as instant file recovery and improved virtual machine recovery, scalability, combined ("2-in-1") backup and replication mechanisms , built-in duplication, centralized management, and more. There are no fees for individual applications and VMs, or agents for licensing, deployment, and maintenance.
Veeam ONE
Efficient, easy-to-use and affordable monitoring and reporting
Veeam ONE ™ is a comprehensive solution that offers efficient and easy-to-use monitoring and reporting functions for VMware and Hyper-V environments. Veeam ONE provides full visibility into the entire virtual infrastructure, more efficient operation and better availability of the virtual environment, as well as more optimal configuration and use of virtual resources.
Veeam ONE combines the capabilities of Veeam Monitor ™, Reporter ™ and Business View ™ to provide the features that virtualization administrators need most:
- Real-time monitoring: Detailed, maintenance-free, 24/7 monitoring of your entire virtual infrastructure provides quick access to information on performance and availability problems, and an extensive knowledge base helps you quickly identify and fix the causes.
- Change Tracking: Log details of changes to your virtual infrastructure (who, what, where, when and how) to help you refine your change routines and analyze unexpected downtime due to certain changes.
- Documentation and Reporting: Automated and on-demand documentation and reporting of virtual infrastructure provide stakeholders with accurate and timely information.
- Capacity planning: Advanced analytical tools enable precise planning of computing capacity. Veeam ONE studies trends, identifies resource surpluses, and provides flexible what-if models. This creates reliable forecast forecasts and resource allocation recommendations to help you make informed decisions about your virtual infrastructure development.
Now an increasingly complex and business-critical VMware environment can be managed with Veeam, a recognized leader in virtualization management and data protection.
Veeam Management Pack ™ for VMware (SCOM)
Monitor VMware environments with Microsoft System Center Secure your investments with Microsoft System Center (SCOM) and manage your physical and virtual environments from a single console with Veeam MP. Nworks Management provides detailed, scalable, agentless monitoring and management of your VMware infrastructure directly from Microsoft System Center, eliminating the need for a separate monitoring platform.
Find out more about VMware management and monitoring with Microsoft SCOM / MOM tools
Veeam Smart Plug-in ™ (SPI) for VMware
Leverage your existing investments in HP Operations Manager and provide operational staff with the ability to monitor your VMware environment 24/7 without the need for specialized training or virtualization experience. Veeam SPI enables distributed, agentless monitoring and management of VMware infrastructure in full cooperation with HP Operations Manager. VMware performance, event, configuration, status, and topology data is fed directly to HP Operations Manager, providing a collective view of the physical and virtual infrastructure from a single console.
Find out more about monitor and manage your VMware environment with HP Operations Manager.